First, the characteristics of smart cards
Compared with magnetic stripe cards, the advantages of smart cards are not only the substantial increase in storage capacity, but also the enhancement and expansion of application functions, and more importantly, the security mechanisms provided by CPUs. The financial IC's security mechanisms include: authentication functions, message authentication, transaction verification, electronic signatures, secure message transmission, application independence, a complete set of key distribution systems, key independence, advanced keys Algorithm and complete key management system.
Because the CPU card can store the password and encryption algorithm in the card, and in addition to the password verification method, the key can be authenticated with a random number and some algorithms, and the key is stored in the card, and readout is prohibited. These security mechanisms greatly increase the security of cards and systems. In addition, the internal SAM module is used to help the POS and self-service terminal devices to complete key storage and algorithm implementation, and also to further improve the security of the system. Therefore, offline transactions must have SAM modules or security chips. Ensure the safety of the system.
In terms of teller management, due to the unique design of the CPU card in terms of security control, the teller CPU card is used to control the secure transaction of the financial terminal. The personal key and information of the teller are encrypted and stored in the CPU card, and cannot be stolen in the encryption process. In this case, the key may not be a card, and the security level is the highest. Therefore, the promotion of the CPU card security control technology in terminal applications such as POS will greatly improve the security of the terminal application.
The security of smart cards is embodied in:
Safe storage: The unique software and hardware structure of the smart card enhances the security of the storage key, and the key is stored in the card in ciphertext mode. It is only allowed when it is used, otherwise it cannot be read at all. Possibility of leaking secret keys due to poor own care.
Safe use: Because the smart card has a built-in signature authentication and encryption and decryption algorithm, the use of the key can be completely completed in the card, and each use of the key needs to be verified before the password is passed, thereby eliminating the leakage of the user in use. The possibility of the key, while the memory card, magnetic card can not do this. In addition, PIN password protection can be set on the smart card. If you enter the wrong PIN code three times during use, the IC card will be locked and you need to unlock the unlock code. If you enter the wrong unlock code three times in a row, the IC card will be automatically invalidated. Can't be used again.
Security generation: A complete set of key generation and key distribution systems are based on the fact that the key can be completely controlled within the card.
According to the principle of security control of data confidentiality, data integrity, and data identifiability in financial transactions, we believe that the use of smart card technology and the introduction of a two-way authentication concept between smart cards in applications can make financial transactions safer. Get effective control and assurance.
1. Data confidentiality: The sensitive data of the user's password needs to be transmitted encrypted to prevent third parties other than the receiver from intercepting the password.
2. Data Integrity: The message authentication code is used to prevent unlawful or malicious counterfeit, tampering, and deletion of illegal users' accounts, amounts, transaction types, host's response processing, etc., of financial transaction messages, preventing data transfer process. Loss and duplication of information ensure the integrity of transaction messages.
3. Data identifiability: The operator electronically signs sensitive data, such as: transaction account number, transaction amount, transaction date and time, transaction terminal number, transaction serial number, etc. for effective electronic signature, providing a reliable identification for the bank host. means.
Second, the application of smart cards will be able to solve some problems in the security control of the financial sector 1. Operators violation of unauthorized operations
In terms of management, personally managed financial terminals currently use operator passwords to control transaction security. In order to facilitate the work, personal passwords are sometimes shared by colleagues. In this case, there may be operator violations.
The financial IC card is to make full use of the "smart" features on its cards, through the security settings and storage of various types of keys and passwords, card and terminal authentication, transaction authentication, electronic signatures, etc., as long as the use of IC card readers on financial terminals The writing ability of the gold card keyboard increases the operator's IC signature capability during the transaction process, and the hidden trouble of the operation of the ultra-privileged authority can be better resolved.
2. Problems in the use of financial magnetic cards
The financial magnetic card itself has the problem of being easily copied. As long as the information on the magnetic track of the magnetic card is read out, a bank card that can be used on self-service equipment such as shopping mall POS and ATM can be copied within a few minutes. Personal information and keys recorded in the IC card can be protected by personal passwords, working keys, etc., and are not illegally copied.
In addition, from a management point of view, after the loss of a financial magnetic card, an illegal cardholder could not say “password is wrong†without changing his/her heart in the wrong password, change the environment and retry the password, and the IC card is In an offline environment, it is also possible to effectively control the number of illegal cardholder test passwords.
From the point of view of the transaction process, although the bank can use the password to identify the cardholder’s authenticity and effectiveness, for the magnetic carder, he cannot identify the bank’s true validity, and the security control of the magnetic card transaction is concentrated on the personal password. Since the transaction message can be analyzed, that is, in some links, if the management control has a problem, the magnetic carder's password is transparent. If the bank's internal staff is in a disadvantage, he can analyze the POS or ATM transaction messages, analyze the user's funds, and analyze the user's password to achieve the purpose of stealing the user's card. If there are illegal banking or illegal banking end devices, hackers can obtain track information and personal passwords of the deceived magnetic card holders, thereby achieving the purpose of illegally creating financial magnetic cards and cashing in the bank's real environment, such as the Guangdong version of the 2001 Gold Card Project. > In the second report, the second fraudulent cash machine financial fraud occurred in Taipei. This financial fraud defrauded the magnetic card reader by placing a private bank's mobile cash machine in a busy city such as Taipei Shilin. The track information and personal passwords illegally defrauded more than four million NT dollars from hundreds of people.
Financial IC card is to make full use of the "smart" features on its cards, through the security settings and storage of various types of keys and passwords, card and terminal authentication, transaction authentication, electronic signatures, etc., through the design of IC card two-way authentication method to identify Banks and cards are real and effective. At the same time, the password modification and verification are performed only in the card and do not need to be transmitted on the network.
3. Credit control
Credit card overdraft or debit card interest income from consumer credit is also an important source of income for bank card business. However, at present, the level of personal credit in China is relatively disparate. Traditional magnetic card technology can not treat each cardholder's credit data to the special merchant's transaction link to treat it differently, mainly by controlling the risk by reducing the universal credit limit. Most credit cardholders’ credit consumption.
Compared with the ordinary magnetic stripe credit card, since the balance and the allowable overdraft limit can be stored on the IC card chip, the customer has a certain credit consumption ability, making offline consumption possible, and avoiding the phenomenon of malignant overdraft of the magnetic stripe card. . The IC card can safely conduct off-line transactions. The IC card stores basic customer information (such as name, type of document, document number), account balance, authorization amount, and PIN of the customer's PIN. During the transaction process, the bank is automatically identified. The validity of the IC card and the recording of the transaction process eliminate the need for complex manual authorization, which simplifies the transaction process and greatly improves the security, speed, and accuracy of the transaction. In addition, transaction data can be used to exchange data with banks via centralized communication methods. The requirements for communications are greatly reduced, which is conducive to increasing the enthusiasm of special merchants to accept bank cards, thereby expanding the application areas of bank cards and improving their use.
Compared with the previous payment methods, the financial smart card, with its unique security features, enables the payment system to ensure that the card cannot be forged, the key will not be leaked, the transaction will not be tampered with, and the bank risk will be minimized. In short, if we use IC cards as a long-term investment for banks, the prospects for their returns are very attractive.
Third, the smart card application security design
The overall security of the financial IC card application system is controlled by the host computer, network, and terminal fully utilizing the IC card security mechanism.
On the one hand, the application design needs to pay attention to the following issues:
1. The keys on personal cards are absolutely decentralized, ie the keys on each card are different.
2. Deposits and debits must use different keys, deposits must be online transaction process, must be strictly controlled: the deposit key must not be stored in the terminal, because the use of software to control security is invalid, for the terminal For engineers with access rights, if the terminal has a deposit key, it can be equivalent to the bank's vault.
3. Two-way authentication is required between the terminal and the card. The terminal needs to check the validity of the IC card. An expired and blacklisted IC card should refuse to execute the transaction and lock the card function, and the card also needs to authenticate the terminal.
4. For financial IC card transactions, transaction details are provided on the card, terminal and financial IC card application system host for future audit.
On the other hand, POS and self-service terminal devices are not as easy to monitor in real-time as the host and the private network within the banking system. The application of IC cards can greatly improve the security control capabilities of terminal devices in financial transactions. In the following, we will discuss smart card security control in the terminal area with the NEWLAND8100POS and NEWLAND8800 card self-service terminals designed by Newland Computer Co., Ltd.
Taking into account the unlimited space for future development of smart cards, the Newland’s NEWLAND8800 card self-service device has an IC card read/write, PSAM card, and contactless smart card reader/writer module in hardware design to meet queries, change passwords, print documents, and recharge cards. The needs of self-service customer service such as IC card enclosing, circling, and self-service payment are applicable to banks, stock exchanges, telecommunication halls, campuses, gas stations, shopping malls, and supermarkets. Another well-built IC boutique NEWLAND8100 new type POS terminal adopts a dedicated security chip, with self-destruction function, and receives PSAM module at the same time, used for storing process keys of financial transactions, with high confidentiality; and for POS machines And the operator's safety management, specially designed the operator IC card holder, meets the application needs of the teller card, can design the CPU card of the teller to store the personal information of the POS and the teller, and sign in the authentication key in the design of the application system. , Used to generate random numbers, encrypt transmission keys, etc. to achieve truly effective security control.
As a transaction for signing the application key, an intelligent operator card is used. After the PIN of the operator card is passed, the work key is applied using the IC private exchange key, so that the transaction key is effectively controlled.
The added PSAM card control module is to effectively control offline transactions: such as the security of deduction keys. Since the process of generating a random number using a cryptographic signature is controlled within the card, the transaction interface between the card and the outside is single, and all transactions are controllable in terms of security. As long as the personalization process of the key is effectively controlled by security, its functional features will not be simulatable and cannot be copied.
For user cards, if lost, there are no security issues. Because of personal PIN protection, the POS equipment or self-service card terminal needs to verify the cardholder's personal PIN when processing the passbook transaction. Since the illegal cardholder does not have a valid password, the wrong password is entered 3 or 6 times in a row. After the IC card will automatically lock the card, and illegal cardholders forcibly unlock the IC, will only lead to the retirement of the IC card. In addition, NEWLAND8100POS and NEWLAND8800 self-service terminal devices manage lost and stolen cards held by illegal cardholders through a large-capacity blacklist.
The authentication key and debit key used to control the user's IC card in the NEWLAND8100POS and NEWLAND8800 self-service terminals are stored on the security chip or SAM card. During the transaction process, the key operation of the authentication or debit is on the security chip or Completed within the SAM card to prevent the leakage of the key. The security chip also has a self-protecting self-destruction function to prevent illegal operations. For the secure management of secure chip keys, the NEWLAND 8100 POS has designed a dedicated program area that is independent of the application software module and is used to change and download the secure chip key of the POS terminal without having to tell the application how to modify the key. At the same time, the NEWLand 8100 POS terminal and NEWLAND 8800 card self-service terminal all have a safe power-off protection function to ensure the security and reliability of transaction record storage.
Prior to the IC card transaction, the IC card can verify the validity of the POS terminal through the security chip or SAM card of the NEWLAND 8100 POS, and the POS can verify the legal validity of the IC card. Since the POS terminal cannot illegally generate an electronic signature of a valid IC card transaction, it is also impossible for the merchant to modify the transaction data that has been completed, and it is impossible to forge transaction data without a user IC card or the user's IC card transaction failure.
For offline IC card change, query balance, check transaction details, with the support of IC card and PSAM card, the transaction process control is performed in the card.
IV. Status Quo of Industry and Application Prospects
The informatization of banks is not merely the acquisition of computers and the erection of networks. In fact, the smart card environment in the field of smart cards and the construction of end devices is also a very important part of information construction.
An IC card system that uses a portable card to store data information can replace the complicated work of many users. The data stored in the IC card can be used as a substitute for things such as banknotes, identity authentication, and passwords, and the convenience of integrating multiple functions cannot be rejected by individual terminal users.
The IC card system is not new in the domestic market. As early as 1993, the domestic construction of the "Gold Card Project" began. The main purpose of the IC card system is to implement the bank's smart card "electronic money" system. So far, the “Gold Card Project†has achieved remarkable results. The financial card reading system has been widely adopted by banks and retail companies, and the application of financial cards has also been accepted by individual consumers.
Due to the security features of the smart card, it will bring several changes to the banking business: 1. Secure offline transactions without complicated manual authorization, simplifying the transaction process, reducing communication requirements, and helping to increase merchant acceptance. Enthusiasm; 2. Improve the level of credit risk control, which is conducive to the development of the market and the promotion of bank card business; 3. The smart card security system provides a strong guarantee for the security control of online consumer, online wealth management, online securities and other services. , Making online personal banking business more business opportunities.
According to the more optimistic forecast of relevant departments, by 2003, about half of online transactions will use smart card technology to ensure security. Mobile phones have adopted smart cards. Banks, retailers, and individual users are very concerned about secure and reliable transaction confirmation for the banking business. The initial reason for France to start switching from magnetic cards to smart cards was fraud. The smart card organization's data in May 1999 showed that since the use of smart cards in France 10 years, the fraud rate has dropped by 10 times, from 0.18 in 1998 to 0.018 in 1999. The number of transactions during this period ranged from 1.197 billion in 1998 to 3.137 billion in 1999. There are now approximately 33 million smart cards circulating in France. Switching to smart card technology will reduce card fraud, especially forgery, while smart cards will also provide more opportunities for cardholder identity verification.
We look forward to the day when our wallets will no longer be filled with all sorts of cards. We can use the same dual interface (contact/contactless) smart card to start the car and access it through physical contact with the security of this card. Log on to the computer, purchase the cake from the cafeteria using the electronic wallet, and use this card to prove your identity in the gymnasium. Of course, these are just some of the possibilities that smart cards have brought us in the new millennium. The broader application prospects still require us all to work together.
(Text / Fujian Newland Computer Co., Ltd. Lan Shuchun)
Compared with magnetic stripe cards, the advantages of smart cards are not only the substantial increase in storage capacity, but also the enhancement and expansion of application functions, and more importantly, the security mechanisms provided by CPUs. The financial IC's security mechanisms include: authentication functions, message authentication, transaction verification, electronic signatures, secure message transmission, application independence, a complete set of key distribution systems, key independence, advanced keys Algorithm and complete key management system.
Because the CPU card can store the password and encryption algorithm in the card, and in addition to the password verification method, the key can be authenticated with a random number and some algorithms, and the key is stored in the card, and readout is prohibited. These security mechanisms greatly increase the security of cards and systems. In addition, the internal SAM module is used to help the POS and self-service terminal devices to complete key storage and algorithm implementation, and also to further improve the security of the system. Therefore, offline transactions must have SAM modules or security chips. Ensure the safety of the system.
In terms of teller management, due to the unique design of the CPU card in terms of security control, the teller CPU card is used to control the secure transaction of the financial terminal. The personal key and information of the teller are encrypted and stored in the CPU card, and cannot be stolen in the encryption process. In this case, the key may not be a card, and the security level is the highest. Therefore, the promotion of the CPU card security control technology in terminal applications such as POS will greatly improve the security of the terminal application.
The security of smart cards is embodied in:
Safe storage: The unique software and hardware structure of the smart card enhances the security of the storage key, and the key is stored in the card in ciphertext mode. It is only allowed when it is used, otherwise it cannot be read at all. Possibility of leaking secret keys due to poor own care.
Safe use: Because the smart card has a built-in signature authentication and encryption and decryption algorithm, the use of the key can be completely completed in the card, and each use of the key needs to be verified before the password is passed, thereby eliminating the leakage of the user in use. The possibility of the key, while the memory card, magnetic card can not do this. In addition, PIN password protection can be set on the smart card. If you enter the wrong PIN code three times during use, the IC card will be locked and you need to unlock the unlock code. If you enter the wrong unlock code three times in a row, the IC card will be automatically invalidated. Can't be used again.
Security generation: A complete set of key generation and key distribution systems are based on the fact that the key can be completely controlled within the card.
According to the principle of security control of data confidentiality, data integrity, and data identifiability in financial transactions, we believe that the use of smart card technology and the introduction of a two-way authentication concept between smart cards in applications can make financial transactions safer. Get effective control and assurance.
1. Data confidentiality: The sensitive data of the user's password needs to be transmitted encrypted to prevent third parties other than the receiver from intercepting the password.
2. Data Integrity: The message authentication code is used to prevent unlawful or malicious counterfeit, tampering, and deletion of illegal users' accounts, amounts, transaction types, host's response processing, etc., of financial transaction messages, preventing data transfer process. Loss and duplication of information ensure the integrity of transaction messages.
3. Data identifiability: The operator electronically signs sensitive data, such as: transaction account number, transaction amount, transaction date and time, transaction terminal number, transaction serial number, etc. for effective electronic signature, providing a reliable identification for the bank host. means.
Second, the application of smart cards will be able to solve some problems in the security control of the financial sector 1. Operators violation of unauthorized operations
In terms of management, personally managed financial terminals currently use operator passwords to control transaction security. In order to facilitate the work, personal passwords are sometimes shared by colleagues. In this case, there may be operator violations.
The financial IC card is to make full use of the "smart" features on its cards, through the security settings and storage of various types of keys and passwords, card and terminal authentication, transaction authentication, electronic signatures, etc., as long as the use of IC card readers on financial terminals The writing ability of the gold card keyboard increases the operator's IC signature capability during the transaction process, and the hidden trouble of the operation of the ultra-privileged authority can be better resolved.
2. Problems in the use of financial magnetic cards
The financial magnetic card itself has the problem of being easily copied. As long as the information on the magnetic track of the magnetic card is read out, a bank card that can be used on self-service equipment such as shopping mall POS and ATM can be copied within a few minutes. Personal information and keys recorded in the IC card can be protected by personal passwords, working keys, etc., and are not illegally copied.
In addition, from a management point of view, after the loss of a financial magnetic card, an illegal cardholder could not say “password is wrong†without changing his/her heart in the wrong password, change the environment and retry the password, and the IC card is In an offline environment, it is also possible to effectively control the number of illegal cardholder test passwords.
From the point of view of the transaction process, although the bank can use the password to identify the cardholder’s authenticity and effectiveness, for the magnetic carder, he cannot identify the bank’s true validity, and the security control of the magnetic card transaction is concentrated on the personal password. Since the transaction message can be analyzed, that is, in some links, if the management control has a problem, the magnetic carder's password is transparent. If the bank's internal staff is in a disadvantage, he can analyze the POS or ATM transaction messages, analyze the user's funds, and analyze the user's password to achieve the purpose of stealing the user's card. If there are illegal banking or illegal banking end devices, hackers can obtain track information and personal passwords of the deceived magnetic card holders, thereby achieving the purpose of illegally creating financial magnetic cards and cashing in the bank's real environment, such as the Guangdong version of the 2001 Gold Card Project. > In the second report, the second fraudulent cash machine financial fraud occurred in Taipei. This financial fraud defrauded the magnetic card reader by placing a private bank's mobile cash machine in a busy city such as Taipei Shilin. The track information and personal passwords illegally defrauded more than four million NT dollars from hundreds of people.
Financial IC card is to make full use of the "smart" features on its cards, through the security settings and storage of various types of keys and passwords, card and terminal authentication, transaction authentication, electronic signatures, etc., through the design of IC card two-way authentication method to identify Banks and cards are real and effective. At the same time, the password modification and verification are performed only in the card and do not need to be transmitted on the network.
3. Credit control
Credit card overdraft or debit card interest income from consumer credit is also an important source of income for bank card business. However, at present, the level of personal credit in China is relatively disparate. Traditional magnetic card technology can not treat each cardholder's credit data to the special merchant's transaction link to treat it differently, mainly by controlling the risk by reducing the universal credit limit. Most credit cardholders’ credit consumption.
Compared with the ordinary magnetic stripe credit card, since the balance and the allowable overdraft limit can be stored on the IC card chip, the customer has a certain credit consumption ability, making offline consumption possible, and avoiding the phenomenon of malignant overdraft of the magnetic stripe card. . The IC card can safely conduct off-line transactions. The IC card stores basic customer information (such as name, type of document, document number), account balance, authorization amount, and PIN of the customer's PIN. During the transaction process, the bank is automatically identified. The validity of the IC card and the recording of the transaction process eliminate the need for complex manual authorization, which simplifies the transaction process and greatly improves the security, speed, and accuracy of the transaction. In addition, transaction data can be used to exchange data with banks via centralized communication methods. The requirements for communications are greatly reduced, which is conducive to increasing the enthusiasm of special merchants to accept bank cards, thereby expanding the application areas of bank cards and improving their use.
Compared with the previous payment methods, the financial smart card, with its unique security features, enables the payment system to ensure that the card cannot be forged, the key will not be leaked, the transaction will not be tampered with, and the bank risk will be minimized. In short, if we use IC cards as a long-term investment for banks, the prospects for their returns are very attractive.
Third, the smart card application security design
The overall security of the financial IC card application system is controlled by the host computer, network, and terminal fully utilizing the IC card security mechanism.
On the one hand, the application design needs to pay attention to the following issues:
1. The keys on personal cards are absolutely decentralized, ie the keys on each card are different.
2. Deposits and debits must use different keys, deposits must be online transaction process, must be strictly controlled: the deposit key must not be stored in the terminal, because the use of software to control security is invalid, for the terminal For engineers with access rights, if the terminal has a deposit key, it can be equivalent to the bank's vault.
3. Two-way authentication is required between the terminal and the card. The terminal needs to check the validity of the IC card. An expired and blacklisted IC card should refuse to execute the transaction and lock the card function, and the card also needs to authenticate the terminal.
4. For financial IC card transactions, transaction details are provided on the card, terminal and financial IC card application system host for future audit.
On the other hand, POS and self-service terminal devices are not as easy to monitor in real-time as the host and the private network within the banking system. The application of IC cards can greatly improve the security control capabilities of terminal devices in financial transactions. In the following, we will discuss smart card security control in the terminal area with the NEWLAND8100POS and NEWLAND8800 card self-service terminals designed by Newland Computer Co., Ltd.
Taking into account the unlimited space for future development of smart cards, the Newland’s NEWLAND8800 card self-service device has an IC card read/write, PSAM card, and contactless smart card reader/writer module in hardware design to meet queries, change passwords, print documents, and recharge cards. The needs of self-service customer service such as IC card enclosing, circling, and self-service payment are applicable to banks, stock exchanges, telecommunication halls, campuses, gas stations, shopping malls, and supermarkets. Another well-built IC boutique NEWLAND8100 new type POS terminal adopts a dedicated security chip, with self-destruction function, and receives PSAM module at the same time, used for storing process keys of financial transactions, with high confidentiality; and for POS machines And the operator's safety management, specially designed the operator IC card holder, meets the application needs of the teller card, can design the CPU card of the teller to store the personal information of the POS and the teller, and sign in the authentication key in the design of the application system. , Used to generate random numbers, encrypt transmission keys, etc. to achieve truly effective security control.
As a transaction for signing the application key, an intelligent operator card is used. After the PIN of the operator card is passed, the work key is applied using the IC private exchange key, so that the transaction key is effectively controlled.
The added PSAM card control module is to effectively control offline transactions: such as the security of deduction keys. Since the process of generating a random number using a cryptographic signature is controlled within the card, the transaction interface between the card and the outside is single, and all transactions are controllable in terms of security. As long as the personalization process of the key is effectively controlled by security, its functional features will not be simulatable and cannot be copied.
For user cards, if lost, there are no security issues. Because of personal PIN protection, the POS equipment or self-service card terminal needs to verify the cardholder's personal PIN when processing the passbook transaction. Since the illegal cardholder does not have a valid password, the wrong password is entered 3 or 6 times in a row. After the IC card will automatically lock the card, and illegal cardholders forcibly unlock the IC, will only lead to the retirement of the IC card. In addition, NEWLAND8100POS and NEWLAND8800 self-service terminal devices manage lost and stolen cards held by illegal cardholders through a large-capacity blacklist.
The authentication key and debit key used to control the user's IC card in the NEWLAND8100POS and NEWLAND8800 self-service terminals are stored on the security chip or SAM card. During the transaction process, the key operation of the authentication or debit is on the security chip or Completed within the SAM card to prevent the leakage of the key. The security chip also has a self-protecting self-destruction function to prevent illegal operations. For the secure management of secure chip keys, the NEWLAND 8100 POS has designed a dedicated program area that is independent of the application software module and is used to change and download the secure chip key of the POS terminal without having to tell the application how to modify the key. At the same time, the NEWLand 8100 POS terminal and NEWLAND 8800 card self-service terminal all have a safe power-off protection function to ensure the security and reliability of transaction record storage.
Prior to the IC card transaction, the IC card can verify the validity of the POS terminal through the security chip or SAM card of the NEWLAND 8100 POS, and the POS can verify the legal validity of the IC card. Since the POS terminal cannot illegally generate an electronic signature of a valid IC card transaction, it is also impossible for the merchant to modify the transaction data that has been completed, and it is impossible to forge transaction data without a user IC card or the user's IC card transaction failure.
For offline IC card change, query balance, check transaction details, with the support of IC card and PSAM card, the transaction process control is performed in the card.
IV. Status Quo of Industry and Application Prospects
The informatization of banks is not merely the acquisition of computers and the erection of networks. In fact, the smart card environment in the field of smart cards and the construction of end devices is also a very important part of information construction.
An IC card system that uses a portable card to store data information can replace the complicated work of many users. The data stored in the IC card can be used as a substitute for things such as banknotes, identity authentication, and passwords, and the convenience of integrating multiple functions cannot be rejected by individual terminal users.
The IC card system is not new in the domestic market. As early as 1993, the domestic construction of the "Gold Card Project" began. The main purpose of the IC card system is to implement the bank's smart card "electronic money" system. So far, the “Gold Card Project†has achieved remarkable results. The financial card reading system has been widely adopted by banks and retail companies, and the application of financial cards has also been accepted by individual consumers.
Due to the security features of the smart card, it will bring several changes to the banking business: 1. Secure offline transactions without complicated manual authorization, simplifying the transaction process, reducing communication requirements, and helping to increase merchant acceptance. Enthusiasm; 2. Improve the level of credit risk control, which is conducive to the development of the market and the promotion of bank card business; 3. The smart card security system provides a strong guarantee for the security control of online consumer, online wealth management, online securities and other services. , Making online personal banking business more business opportunities.
According to the more optimistic forecast of relevant departments, by 2003, about half of online transactions will use smart card technology to ensure security. Mobile phones have adopted smart cards. Banks, retailers, and individual users are very concerned about secure and reliable transaction confirmation for the banking business. The initial reason for France to start switching from magnetic cards to smart cards was fraud. The smart card organization's data in May 1999 showed that since the use of smart cards in France 10 years, the fraud rate has dropped by 10 times, from 0.18 in 1998 to 0.018 in 1999. The number of transactions during this period ranged from 1.197 billion in 1998 to 3.137 billion in 1999. There are now approximately 33 million smart cards circulating in France. Switching to smart card technology will reduce card fraud, especially forgery, while smart cards will also provide more opportunities for cardholder identity verification.
We look forward to the day when our wallets will no longer be filled with all sorts of cards. We can use the same dual interface (contact/contactless) smart card to start the car and access it through physical contact with the security of this card. Log on to the computer, purchase the cake from the cafeteria using the electronic wallet, and use this card to prove your identity in the gymnasium. Of course, these are just some of the possibilities that smart cards have brought us in the new millennium. The broader application prospects still require us all to work together.
(Text / Fujian Newland Computer Co., Ltd. Lan Shuchun)
1.4 inch Medium Duty Caster Wheel , Fixed / Swivel / Brake
2.High quality galvanized support
3.Single wheel PVC / PU / TPR / PVC material
4.Double ball bearings caster wheels
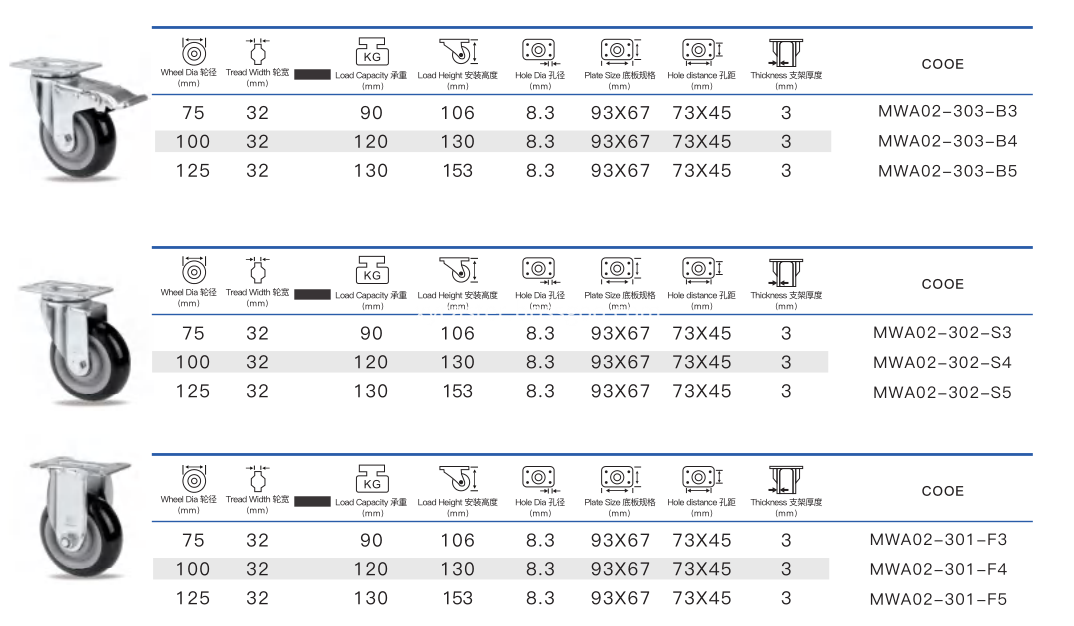
4 Inch Medium Duty Caster Wheels, 4 Inch Medium Duty Casters,Industrial Castor Wheels,4 Inch Swivel Type Caster
Yangjiang Xingyang Industry & Trade Co.,Ltd. , https://www.xycaster.com